Actions is a continuous integration and continuous delivery (CI/CD) feature that allows you to automate your build, test and deployment pipelines in Forgejo, the software Codeberg uses. For more information, please read Forgejo's Documentation.
Due to outstanding security issues and bus factor (we need more maintainers for our CI service), we are currently providing hosted Actions in limited fashion: see https://codeberg.org/actions/meta. If you need Codeberg to host your CI, please use Woodpecker CI instead.
But you can already connect your own Runner to Codeberg. CI jobs will run on your machine, and the result will be displayed in Codeberg. The Runner does not need a public IP address since it will connect to Codeberg and then wait for jobs to run. So you can even run it on a machine in your home.
This guide will walk you through setting up your own Forgejo Actions Runner to use for CI jobs.
Obtaining a registration token
Repository Actions are disabled by default and will require you to enable them in the "Units" > "Overview" section of your repository's settings page.
Before deploying the Runner, you need to obtain a registration token from Codeberg. Registration tokens are used by the Runner and Codeberg to share secrets and configurations.
You can add Runners to your account, organization, or repository. Choosing where you obtain the registration token will determine where your Runner will accept workflows from.
-
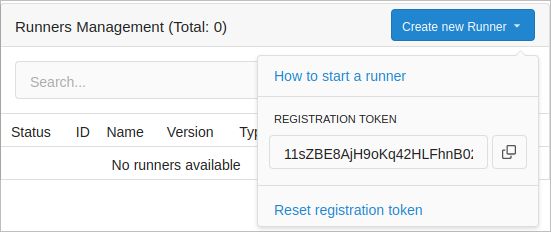
Go to the account/organization/repository settings page.
-
Click on Actions.
-
Click on Runners.
-
Click on Create new Runner.
-
Copy the registration token.
Installing Forgejo Runner
For the installation of the runner, see the Forgejo documentation.